Suspicious Activity Monitoring
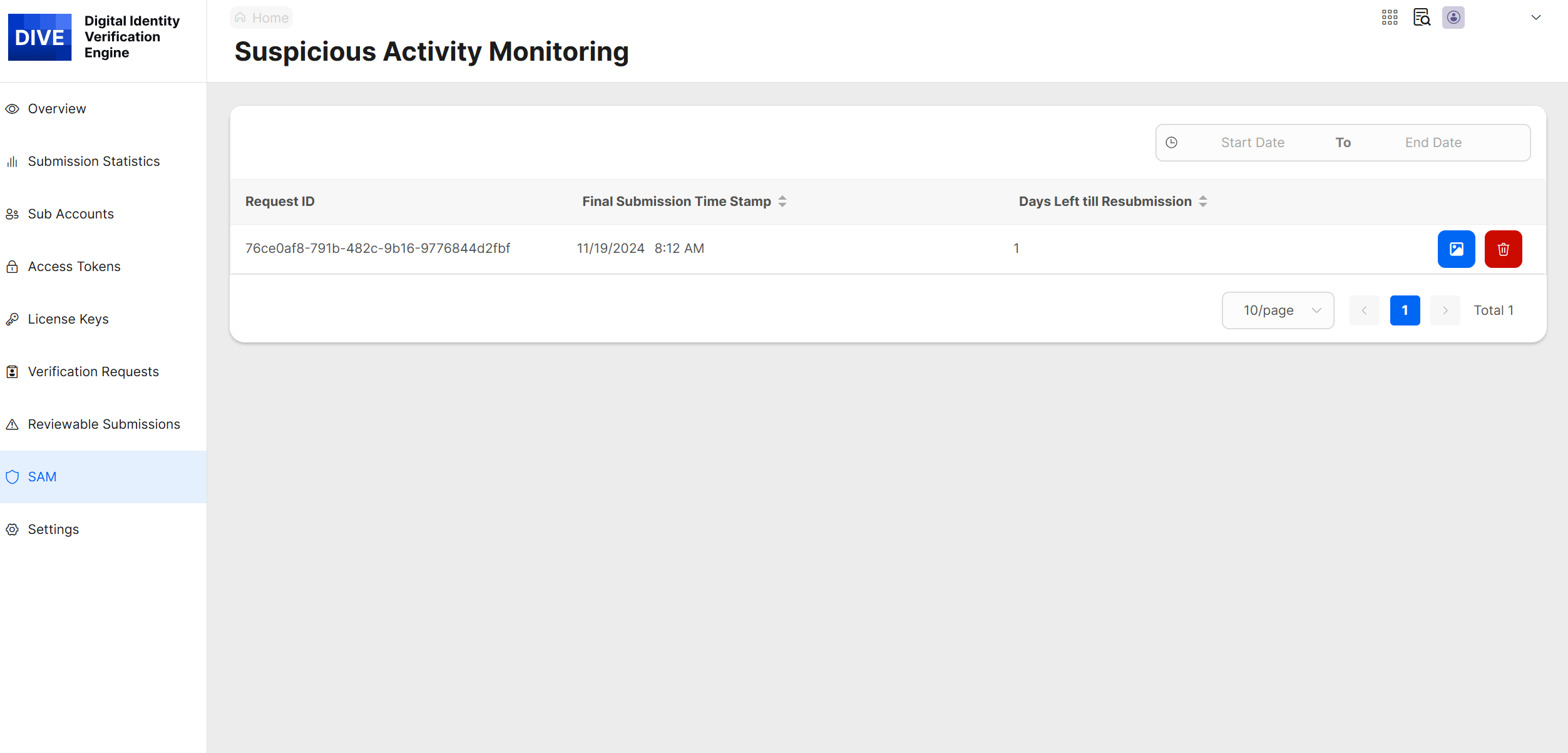
The Suspicious Activity Monitoring log will display all the sets of images that have been rejected. All unique sets of images that have been submitted the amount of times needed to exceed the configured threshold will be displayed in the table on this page.
- Most Recent Request ID that has been rejected
- Most Recent Timestamp of the Submitted Images
- The Number of Days that the Images will be Rejected
- The Number of Times the Images Have been Rejected